· Industrial Cybersecurity · 3 min read
OT Cybersecurity: From the Purdue Model to IEC 62443
Being "disconnected" is no longer an option. Learn to design a robust industrial network using Zones and Conduits to protect your critical assets.
For decades, plant-floor cybersecurity followed the “Air Gap” rule: “If the PLC isn’t on the internet, it can’t be hacked”. Today, with the rise of IIoT, remote maintenance, and cloud-based MES systems, the Air Gap is dead.
Modern industrial cybersecurity is not about putting in a firewall and forgetting about it. It’s about defense in depth. In this technical guide, we explore how to move from a theoretical diagram (Purdue) to a real implementation (IEC 62443).
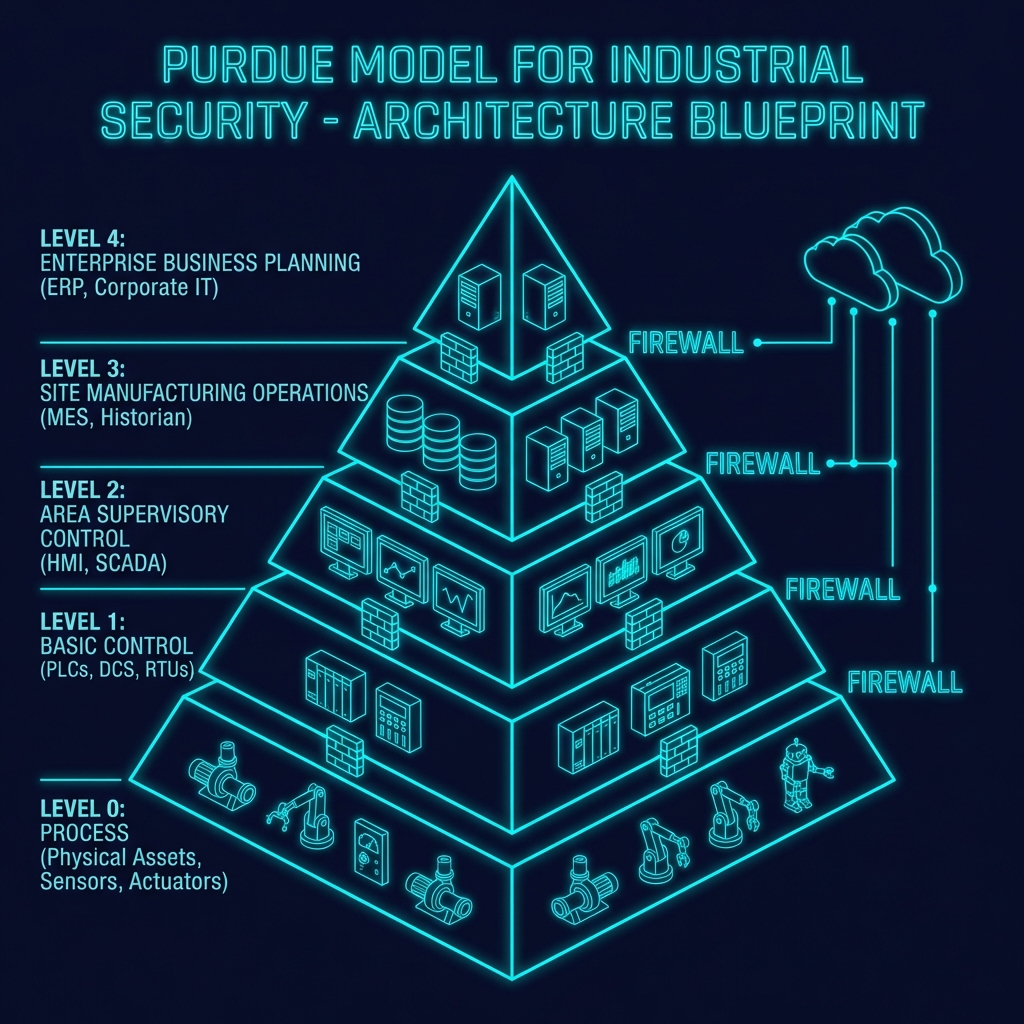
1. The Purdue Model: The Foundation of Hierarchy
The Purdue Model (ISA-95) tells us where systems live. It is fundamental for understanding hierarchy:
graph TD
subgraph "Level 4-5: Enterprise (IT)"
Cloud[Cloud / ERP]
end
subgraph "Level 3.5: DMZ"
Firewall1[IT/OT Firewall]
end
subgraph "Level 3: Operations"
MES[MES / Historian]
end
subgraph "Level 1-2: Control"
SCADA[SCADA / HMI]
PLC[PLC Controllers]
end
subgraph "Level 0: Process"
Sensors[Sensors / Actuators]
end
Cloud --- Firewall1
Firewall1 --- MES
MES --- SCADA
SCADA --- PLC
PLC --- Sensors2. IEC 62443: Zones and Conduits
While Purdue tells you the levels, the IEC 62443 standard tells you how to protect the communication between them. The key concept is Zones & Conduits:
- Zone: A group of assets (PLCs, HMIs) with similar security requirements.
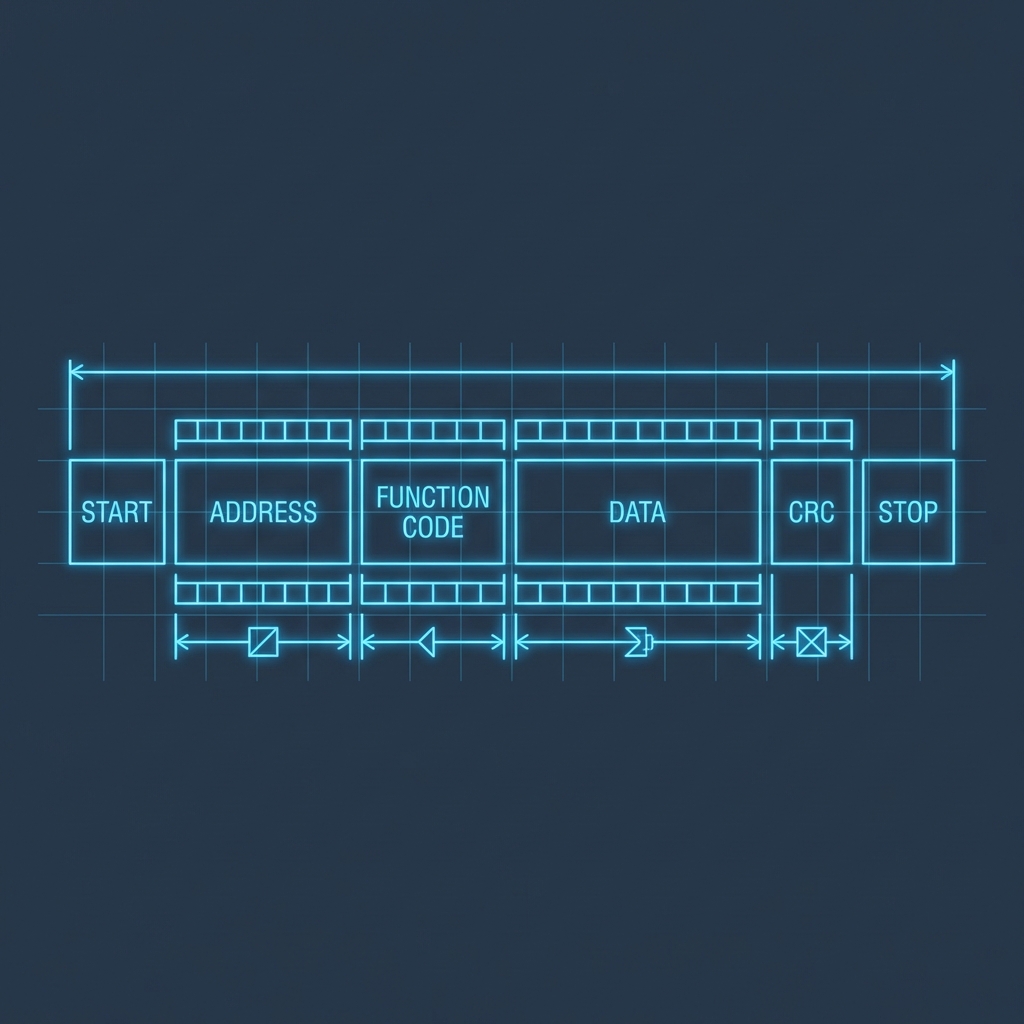
- Conduit: The communication path between zones. This is where you apply industrial firewalls (e.g., FortiGate Rugged, Stratix) and Deep Packet Inspection (DPI) for Modbus or Profinet.
[!IMPORTANT] A PLC should never talk directly to the ERP. It must always pass through a gateway or a historian in an industrial DMZ (Level 3.5).
3. Asset Hardening Checklist
If you have a PLC on your network, ask yourself these questions:
- Unnecessary Ports? Is the PLC’s web server or FTP enabled? If you don’t use it, disable it.
- Authentication? Do your PLCs have a password for program downloads? (Siemens S7-1500 asks for it by default, older PLCs don’t).
- Physical Segmentation? Are you mixing security camera traffic with control traffic? Use VLANs or managed switches.
4. The Human Factor: Remote Access
80% of attacks on critical infrastructure enter through poorly configured remote access.
- Don’t use Port Forwarding. Never open PLC port
502directly to the internet. - Use Industrial VPNs: Solutions like Ewon Cosy or HMS Anybus that create outbound tunnels are much more secure than traditional VPNs.
Conclusion
OT cybersecurity is a balance between availability and protection. If your firewall blocks an emergency message that stops a boiler, your system is safe but useless. Intelligent segmentation using IEC 62443 is the only way to scale your IIoT projects without risk.
Official Sources and Guides: